Imagine a mystical world where data is safeguarded by potent cryptographic sorcery known as "hashing." In this enchanting realm of cybersecurity, we embark on a quest to demystify the basics of hashing before we delve into the powerful tool called Hashcat.
Part I: The Magical Art of Hashing
Chapter 1: The Enchanted Hash Function
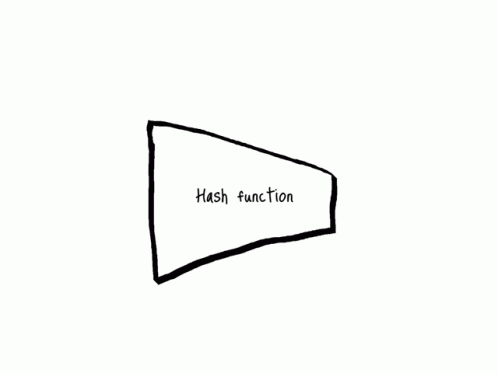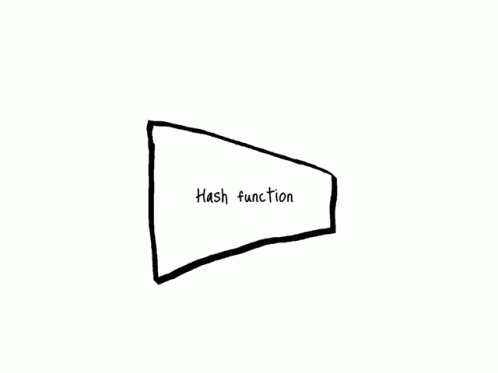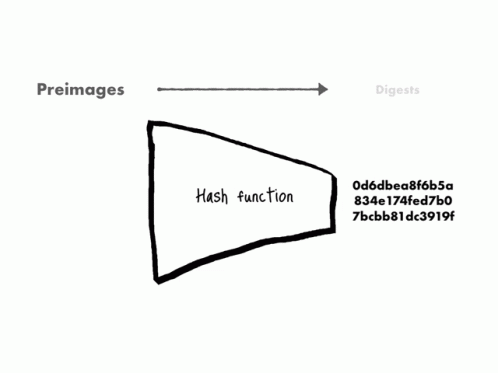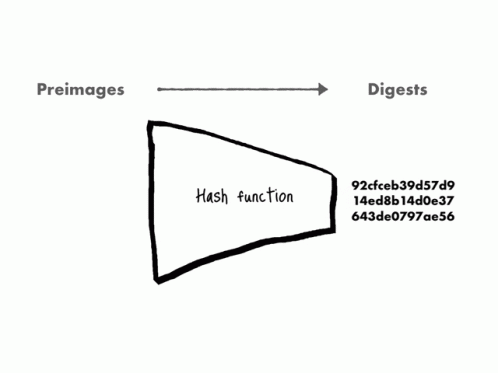
In the magical world of computing, a "hash function" is a wondrous spell that turns any information into a unique and fixed-size code, like a magical fingerprint. It's fast, secure, and helps organize the mystical realm of data.
Chapter 2: The Inscrutable One-Way Street
The one-way nature of hashing lies in its irreversible enchantment. The process does not keep track of the original data's details, making it practically impossible to reverse the magic and retrieve the exact original content from the hash code alone. It's like the spell erases any clues needed to find the way back, ensuring the mystical realm of data remains secure and hidden from prying eyes.

Chapter 3: Decrypting the Hashes
In the mystical realm of cybersecurity, where secrets are locked away behind the impenetrable walls of hashed codes, Hashcat emerges as the valiant hero, armed with unparalleled sorcery to decrypt these enigmatic cyphers.
Hashcat is a powerful and popular open-source password recovery tool, designed to crack or recover passwords from hashed data using various attack methods. It is often used to test the strength of passwords and assess the security of systems.
Hashcat can take hashed passwords, along with information about the hashing algorithms used, and then systematically attempt different combinations of characters to guess the original passwords. It utilizes the computing power of modern CPUs and GPUs to perform these password-cracking attacks efficiently and quickly.
The tool supports various attack modes, such as dictionary attacks (using a list of common passwords), brute-force attacks (trying all possible combinations), and rule-based attacks (applying custom transformation rules to wordlists).
Its basic usage takes 4 arguments.
Argument 1 of 4 :
-m(or --hash type)
The -m (or --hash type) option in Hashcat lets users specify the type of hash algorithm used to encrypt passwords, ensuring efficient and accurate password recovery attempts for the chosen algorithm.
ex. MD5,SHA-1, Kerberos 5 etc.
To view the full list of available hash algorithms in Hashcat, use the command
--helpin the terminal.Hashcat offers an impressive selection of more than 237 different hash algorithms.
ex.
-m 5800Samsung Android Password/PINThe "-m 5800" option represents the hash mode for cracking Samsung Android passwords or PINs. It indicates that hashcat is set up to handle and attempt to decrypt the hashed passwords or PINs used in Samsung Android devices.
Resources:
--hash type values for hashcat : https://hashcat.net/wiki/doku.php?id=hashcat
to check which algo to use: https://www.tunnelsup.com/hash-analyzer/
Argument 2 of 4 :
The "-a" (or "--attack-mode") option in Hashcat allows you to select the attack mode, determining the method of cracking passwords, like dictionary, brute-force, or rule-based attacks.
Dictionary Attack:
hashcat -a 0Brute-Force Attack:
hashcat -a 3Combinator Attack:
hashcat -a 1
Rule-Based Attack: hashcat -a 6
Argument 3 of 4:
Using a filename:
hashcat [filename] wordlist.txtBy providing a filename, like "hashes.txt," you can crack the hashed passwords stored in that file using words from "wordlist.txt."(or Dictionary, we will dive deeper after)
Using a Hash Directly:
hashcat [hash] wordlist.txtYou can also directly input a hash value, such as "5f4dcc3b5aa765d61d8327deb882cf99," and attempt to crack it using the words from the "wordlist.txt" wordlist.Combining Both:
hashcat --force [filename|hash] wordlist.txtBy using "[filename|hash]" in the command, hashcat allows you to choose whether the input data is a filename or a hash, and then it will use words from "wordlist.txt" to crack
Argument 4 of 4:
The "[dictionary|mask directory]" syntax in hashcat allows you to specify the input data as either a dictionary file or a directory containing mask files for hash cracking.
Using a Dictionary File:
hashcat [dictionary] hashes.txtBy providing a dictionary file, such as "wordlist.txt," you can attempt to crack the hashed passwords stored in "hashes.txt" using the words from the dictionary.Using a Mask Directory:
hashcat [mask directory] hashes.txtInstead of a dictionary, you can use a directory containing mask files (e.g., "masks/") to perform custom brute-force attacks on the passwords stored in "hashes.txt."Utilizing Both:
hashcat -a 6 [dictionary|mask directory] hashes.txt -r rules.ruleCombining "[dictionary|mask directory]" with the rule-based attack mode (mode 6), hashcat enables you to apply rules from "rules.rule" to the words in the dictionary or masks from the directory, cracking the hashed passwords in "hashes.txt."
Putting it all together:
hashcat -m [hash algo] -a [attack mode] [hashes.txt] [dictionary|mask directory]
hashcat: Invokes the hashcat program for password cracking.-m [hash algo]: Specifies the hash algorithm using the corresponding number.For example, "
-m 0" forMD5,"-m 1000" forNTLM, etc.-a [attack mode]: Specifies the attack mode using the corresponding number.For example, "
-a 0" for dictionary attack, "-a 3" for brute-force attack, etc.[hashes.txt]: Replace this with the filename containing the hashed passwords you want to crack.[dictionary|mask directory]: Replace this with either the path to your dictionary file (e.g., wordlist.txt) or the directory containing mask files for custom brute-force attacks (e.g., masks/).
Make sure to replace the placeholders ([hash algo], [attack mode], [hashes.txt], [dictionary|mask directory]) with the actual values and file paths based on your specific use case.


How to Defend Against Hashcat
The first and obvious step is to set strong passwords. The stronger the password is, the harder it is to crack it. You can check if your password has been exposed to the internet here.
A more effective way is to add salts to password hashes. A salt is an additional string added to the existing password so the hash generated is different from the normal hash of a string.
For example, if a string “sdf909” is added to a password “Password123”, Rainbow table attacks will immediately fail since they don't have hashes with the salt added to them.
To crack a salted password, the attacker should know both the hash and salt values. This makes it harder to crack hashes using methods such as Rainbow tables.
We can further strengthen salting by using dynamic salts instead of static salts. We can write a function that generates a salt value for every string making it exponentially harder to crack a salted password.
You can read this article to learn more about how Salts work in password hashing.
Summary
Hashing is the method of using a mathematical function to generate a random string. It is a one-way function and helps to secure data such as user passwords.
Hashcat is a powerful tool that helps to crack password hashes. Hashcat supports most hashing algorithms and can work with a variety of attack modes.
To enforce security and protect hashes from attacks, use strong passwords and salts before hashing passwords.
